Jun 21, 2016 ☰Menu SSH and Transfer Files using Putty Private Key (.ppk) 21 June 2016. For a concise summary, skip to the end! Recently, I was given access to a server which requires key authentication using a PuTTY key (with the extension.ppk). Question: When Generating And Storing SSH Private Key Pairs, The Following Permissions Mask Is Required. Using This Mask Prevents Unauthorized Access And Is Enforced By The Ssh Agent When Loading Keys. 600 666 000 011 If Key Based Authentication Has Been Enabled Within The SSH Server Configuration, Local Users May Place Keys In This File To Authorize Those Keys. Find out how to protect your server's sensitive data by learning how SSH keys work, creating an SSH key pair, and creating FTP users in SiteWorx. Hosted private cloud on enterprise hardware, powered by VMware & NetApp. Server Clusters. Multi-server configurations for maximum uptime & performance.
- Ssh Private Key Vs Public Key
- Ssh Private Key Passphrase
- Windows 10 Ssh Private Key
- Ssh Private Key File
- Ssh Private Key Authentication
For a concise summary, skip to the end!
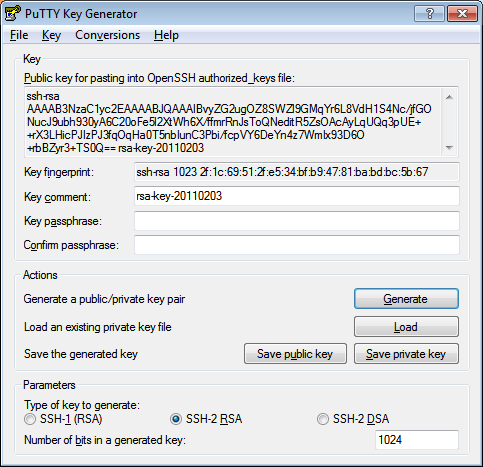
Recently, I was given access to a server which requires key authentication using a PuTTY key (with the extension .ppk).
So I tried the usual:
But it asked me for a passphrase, which I never set:
After some digging around, it turns out PuTTY uses a different key format than the de facto standard - OpenSSH.
Sep 19, 2019 Your private key. For more information about generating a key on Linux or macOS, see Connect to a server by using SSH on Linux or Mac OS X. Log in with a private key. Using a text editor, create a file in which to store your private key. This example uses the file deploymentkey.txt. To edit the file in vim, type the following command. Some elaboration on the above answers to provide a clear path for both the public and private key. You can directly export (-e) your ssh keys to a pem format: For your public key: cd /.ssh ssh-keygen -e -m PEM idrsa idrsa.pub.pem For your private key: Things are a little tricker as ssh-keygen only allows the private key file to be change.
Because of this, ssh didn't recognise the key format and assumed it was encrytped by a passphrase.
So there are two ways you can use the PuTTY key to login to the server and/or transfer files:
- Convert the PuTTY private key (
.ppk) to a PEM-formatted file (the 'normal' private key format used by OpenSSH) andssh/sftpin the usual way; or - Use a PuTTY SSH client to login and
pscpto transfer files
Converting the .ppk to PEM
This is probably the most convenient way as you only have to run one command and everything would be like it was before:
Now you can run the command again as before, but this time you should be granted access automatically.
The same is true for sftp:
Use a PuTTY SSH client to login and pscp to transfer files
Login using PuTTY SSH Client
First, download the PuTTY SSH Client. If you're using a Linux distribution, check the package repositories as well (PuTTY is such an old ancient program you practically don't need to ensure it's up-to-date)

Open up the client and under Session, input your host's name or IP address. If you're server's default SSH port has been changed, input the port number too.
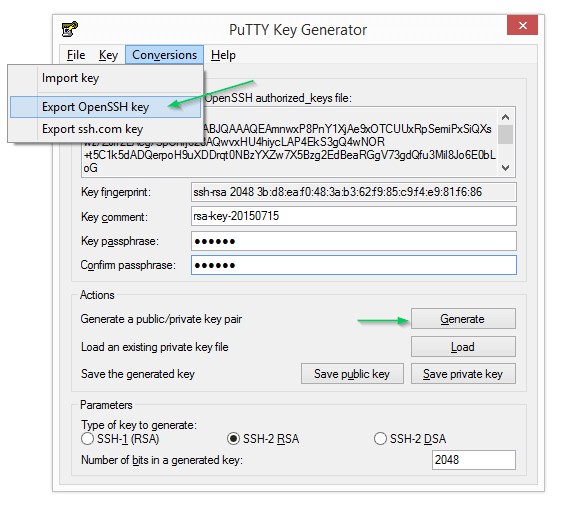
Next, go to SSH > Auth and browse for your private key.
After that, click 'Open'.
It will prompt you for the username, enter it
and if your credentials are correct, be given access to the server.
Transferring Files using pscp
Transferring files the pscp command is similar to using the sftp command:

The -r flag tells pscp to transfer all the files recursively inside the directory, sftp forces pscp to use the the SFTP protocol (instead of SCP) and the -i flag allows you to specify the key to use.
Read about the Difference between the SCP and SFTP Protocols on SuperUser.
For a full list of options, run pscp -h
Summary
To login using a .ppk key, you can:
Convert it to a PEM-formatted OpenSSH key and use
sshnormally:Download and use the PuTTY client
To transfer files using a .ppk key, you can:
Ssh Private Key Vs Public Key
Convert it to a PEM-formatted OpenSSH key and use
sshnormally:Use
pscp
In every SSH/SFTP connection there are four keys (or two key-pairs) involved. This article explains a difference between them and what keys an SFTP client user needs to care about.
The SSH employs a public key cryptography. A public-key cryptography, also known as asymmetric cryptography, is a class of cryptographic algorithms which requires two separate keys, one of which is secret (or private) and one of which is public.1 Together they are known as a key-pair. In SSH, the public key cryptography is used in both directions (client to server and server to client), so two key pairs are used. One key pair is known as a host (server) key, the other as a user (client) key.
A user private key is key that is kept secret by the SSH user on his/her client machine. The user must never reveal the private key to anyone, including the server (server administrator), not to compromise his/her identity.
To protect the private key, it should be generated locally on a user’s machine (e.g. using PuTTYgen) and stored encrypted by a passphrase. The passphrase should be long enough (that’s why it’s called passphrase, not password) to withstand a brute-force attack for a reasonably long time, in case an attacker obtains the private key file.
Different file formats are used to store private keys. WinSCP supports PuTTY format, with .ppk extension.
A user public key is a counterpart to user private key. They are generated at the same time. The user public key can be safely revealed to anyone, without compromising user identity.
To allow authorization of the user on a server, the user public key is registered on the server. In the most widespread SSH server implementation, the OpenSSH, file ~/.ssh/authorized_keys is used for that.
Learn more about public key authentication in general and how to setup authentication with public keys.
Ssh Private Key Passphrase
Advertisement
Windows 10 Ssh Private Key
A host private key is generated when the SSH server is set up. It is safely stored in a location that should be accessible by a server administrator only. The user connecting to the SSH server does not need to care about host private key in general.
A host public key is a counterpart to host private key. They are generated at the same time. The host public key can be safely revealed to anyone, without compromising host identity.
Ssh Private Key File
To allow authorizing the host to the user, the user should be provided with host public key in advance, before connecting. The client application typically prompts the user with host public key on the first connection to allow the user to verify/authorize the key. The host public key is then saved and verified automatically on further connections. The client application warns the user, if the host key changes.
Ssh Private Key Authentication
- The text is partially copied from Wikipedia article on Public-key cryptography. The text is licensed under GNU Free Documentation License.Back

Comments are closed.